
SD-WAN Firewall
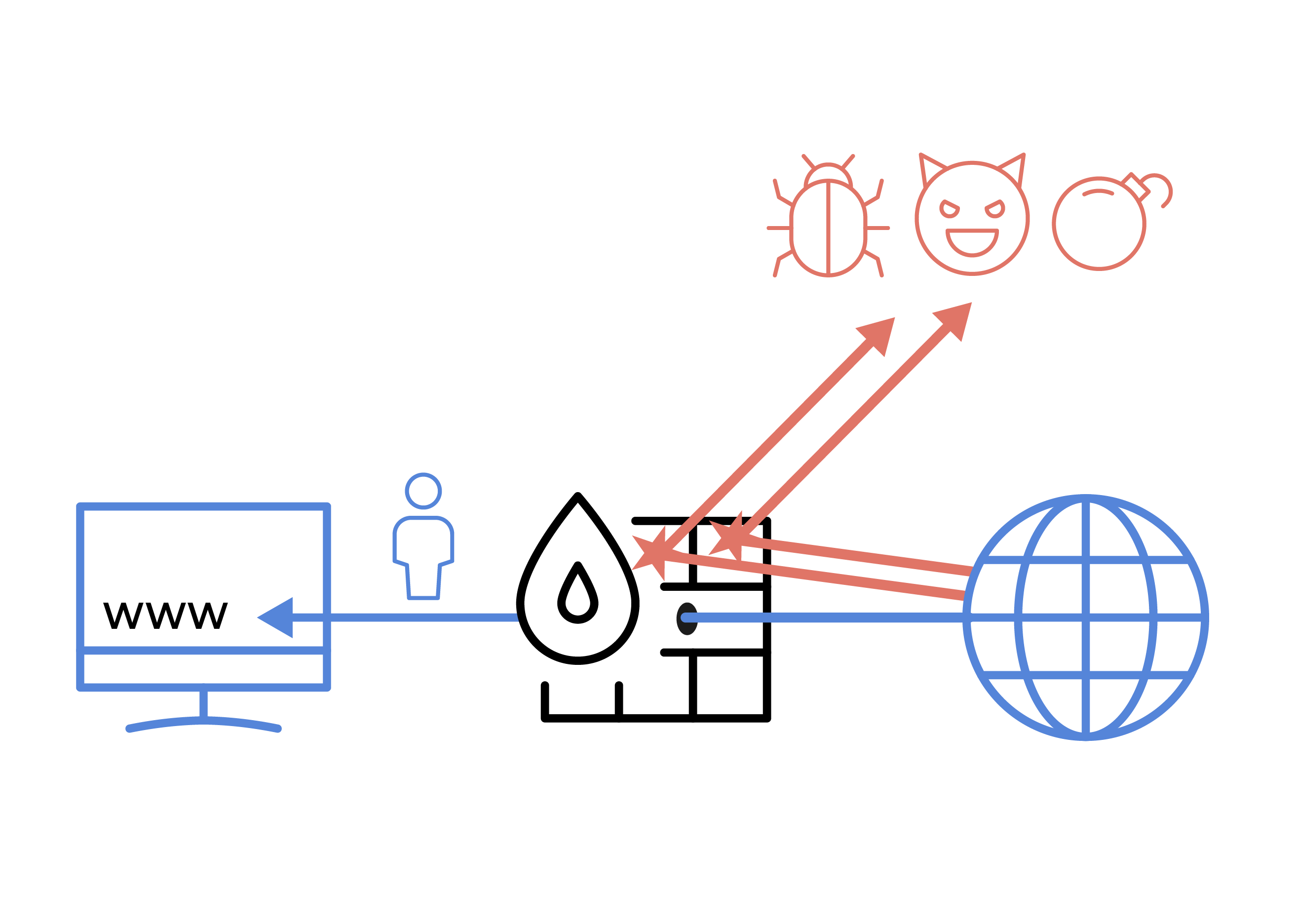
Protect against external threats
Protect WANs from external threats with our next-gen firewall blocking malicious traffic and implementing a powerful policy management concept which avoids security gaps caused by complex policies.
Built-in IDS and hybrid policy management allows organizations to have extensive traffic monitoring, threat detection and response, as well as easy-to-maintain firewall service.
How We Protect Your Network
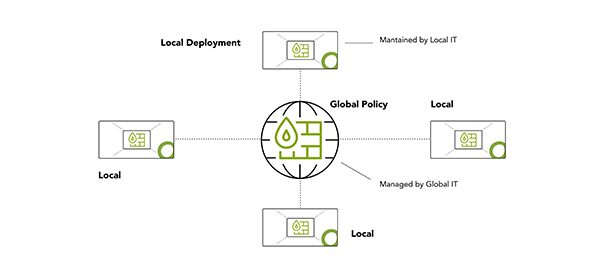
- Global IT defines a global corporate security policy by defining general zone transitions
- Local IT maintains and updates local firewall objects. In addition, exceptions or new zones can be defined in collaboration with global IT.
Advanced filtering
Through deep packet inspection, applications can be detected automatically on the network and used for filtering by the firewall. This helps to simplify the firewall policy – instead of implementing several firewall rules to allow SaaS application traffic with different protocols, ports, and destination IPs, logic can be summarized to one application rule.
Through deep packet inspection, applications can be detected automatically on the network and used for filtering by the firewall. This helps to simplify the firewall policy – instead of implementing several firewall rules to allow SaaS application traffic with different protocols, ports, and destination IPs, logic can be summarized to one application rule.
Threat Protection
Open Systems curates and maintains a block list of malicious domains to automatically prevent access to the constantly evolving threat landscape.
Organizations with Open Systems’ Firewall, Secure Web Gateway and Secure Email Gateway benefit from this unified layer of protection, included as part of the service.
Open Systems curates and maintains a block list of malicious domains to automatically prevent access to the constantly evolving threat landscape.
Organizations with Open Systems’ Firewall, Secure Web Gateway and Secure Email Gateway benefit from this unified layer of protection, included as part of the service.
IDS
Built-in Intrusion Detection System (IDS) enhances traffic visibility by providing real-time monitoring, detection and remediation of potential threats.
Open Systems’ NOC can proactively triage, investigate and engage in remediation scenarios for a 24/7 Network Detection and Response (NDR) coverage.
Built-in Intrusion Detection System (IDS) enhances traffic visibility by providing real-time monitoring, detection and remediation of potential threats.
Open Systems’ NOC can proactively triage, investigate and engage in remediation scenarios for a 24/7 Network Detection and Response (NDR) coverage.
Management
Through the zoning concept, a lot of different network segments or interfaces can be summarized to one zone of a certain security level. Consequently, one simple zone transition policy can be defined instead of implementing several different access rules for each one-to-one communication.
From a policy management perspective, we offer a hybrid administration model that allows an organization’s global IT to enforce a security policy while providing flexibility for local IT to customize the policy where needed.
Through the zoning concept, a lot of different network segments or interfaces can be summarized to one zone of a certain security level. Consequently, one simple zone transition policy can be defined instead of implementing several different access rules for each one-to-one communication.
From a policy management perspective, we offer a hybrid administration model that allows an organization’s global IT to enforce a security policy while providing flexibility for local IT to customize the policy where needed.
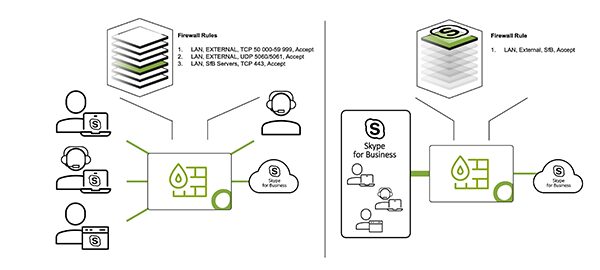
Through deep packet inspection, applications can be detected automatically on the network and used for filtering by the firewall. This helps to simplify the firewall policy – instead of implementing several firewall rules to allow SaaS application traffic with different protocols, ports, and destination IPs, logic can be summarized to one application rule.

Open Systems curates and maintains a block list of malicious domains to automatically prevent access to the constantly evolving threat landscape.
Organizations with Open Systems’ Firewall, Secure Web Gateway and Secure Email Gateway benefit from this unified layer of protection, included as part of the service.
Built-in Intrusion Detection System (IDS) enhances traffic visibility by providing real-time monitoring, detection and remediation of potential threats.
Open Systems’ NOC can proactively triage, investigate and engage in remediation scenarios for a 24/7 Network Detection and Response (NDR) coverage.
Through the zoning concept, a lot of different network segments or interfaces can be summarized to one zone of a certain security level. Consequently, one simple zone transition policy can be defined instead of implementing several different access rules for each one-to-one communication.
From a policy management perspective, we offer a hybrid administration model that allows an organization’s global IT to enforce a security policy while providing flexibility for local IT to customize the policy where needed.
- Global IT defines a global corporate security policy by defining general zone transitions
- Local IT maintains and updates local firewall objects. In addition, exceptions or new zones can be defined in collaboration with global IT.
IT Leaders Rely on Managed SASE For Secure Connectivity
Read Gartner Peer Insights to see why we’ve earned a 97% customer retention rate.

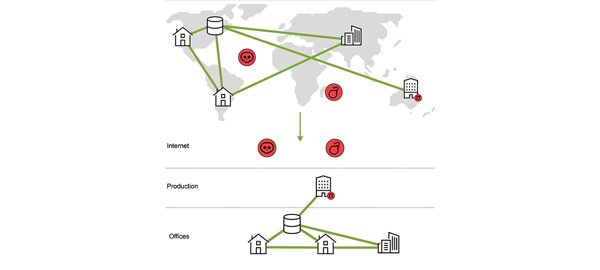
A Multi-Zone Approach Ensures Security and Trust
Open Systems’ firewall architecture introduces distinct security zones. These zones segment the global network into different zones of security and trust and enable communication between zones to be properly controlled.
With this feature, we can filter traffic at transitions between different security zones and maintain security within each zone. Thus, the overall integrity of the SD-WAN can be shielded not only from internet threats but also from doubtful internal sources in untrusted security zones.
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us



